
In today’s digital landscape, malware poses a significant threat to individuals and organizations alike. One particularly dangerous type of malware is worms. Worms are a type of self-replicating malware designed to spread from one computer to another, often through network connections. They can cause significant damage by consuming network bandwidth, overloading systems, and stealing sensitive information. In this blog post, we will discuss advanced strategies for detecting and mitigating worm malware.
Before we dive into detecting and mitigating worms, it is essential to understand how they work. Unlike traditional viruses, worms do not require human interaction to spread. They can replicate themselves and spread through networks, making them highly efficient at infecting multiple systems.
Worms can also exploit vulnerabilities in software and operating systems to gain access to a system and spread further.

The first step in mitigating worm malware is to detect its presence. Traditional antivirus software may not be enough to detect and prevent worms, as they can often bypass these defenses. Therefore, it is crucial to have advanced malware detection tools in place. These tools can detect unusual network activity, identify malicious file signatures, and monitor system processes for any suspicious behavior.
Another essential aspect of detecting worm malware is to keep all software and operating systems up to date. As mentioned earlier, worms can exploit vulnerabilities in software to spread.
By regularly updating software and operating systems, these vulnerabilities can be patched, making it more challenging for worms to infect a system.
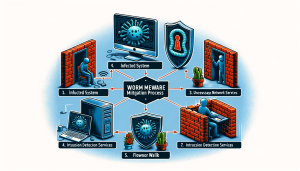
Once a worm has been detected, it is crucial to take immediate action to mitigate its impact. The first step is to isolate the infected system from the network. This will prevent the worm from spreading to other systems. It is also essential to shut down any unnecessary network services to reduce the worm’s ability to spread through the network.
Another effective mitigation strategy is to use intrusion detection and prevention systems. These systems can detect and block malicious network activity, preventing the worm from communicating with its command and control server. Additionally, firewalls can be configured to restrict network traffic to and from infected systems, further containing the worm’s spread.

Controlling network access is another crucial strategy in mitigating worm malware. By limiting network access to only authorized users and devices, the chances of a worm spreading through the network are significantly reduced. Network segmentation, where different parts of the network are separated, can also help contain a worm’s spread if one part of the network is infected.
Another important aspect of controlling network access is implementing strong password policies. Worms often use brute force attacks to gain access to systems and networks. By enforcing strong password policies, such as using complex and unique passwords, the chances of a worm gaining unauthorized access are reduced.

Last but certainly not least, educating users is a crucial strategy in detecting and mitigating worm malware. Users are often the weakest link in the cybersecurity chain, as they can unknowingly download and install malicious software.
Therefore, it is essential to train users on how to identify and report suspicious emails and websites. Regular security awareness training can go a long way in preventing worms and other malware from infecting a system.
Worm malware is a significant threat that can cause significant damage to individuals and organizations. By understanding how worms work and implementing advanced detection and mitigation strategies, we can reduce the chances of falling victim to these malicious attacks. It is crucial to stay vigilant, keep software and systems up to date, and educate users on the importance of cybersecurity. By working together, we can better protect ourselves and our networks from worm malware.